This series of tutorials is aimed to share the notes taken while I was learning python for cybersecurity with the books - Black Hat Python.
這系列教學文章為學習筆記+延伸資源,旨在分享學習書籍 Black Hat Python時所思所學,也希望能幫助想了解Python和資安的大大們入門。
This tutorail has also been written in English in Medium.
Let's get started! 開始吧!
✨ ASCII表也可參照ascii-code.com
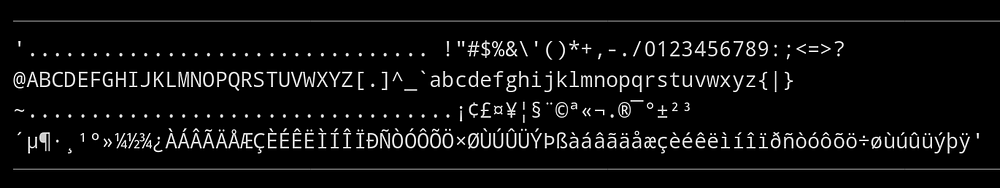
''.join([(len(repr(chr(i))) == 3) and chr(i) or '.' for i in range(256)])
# proxy.py
import sys
import socket
import threading
HEX_FILTER = ''.join([(len(repr(chr(i))) == 3) and chr(i) or '.' for i in range(256)])
def hexdump(src, length=16, show=True):
if isinstance(src, bytes):
src = src.decode()
results = list()
for i in range(0, len(src), length):
word = str(src[i:i+length])
printable = word.translate(HEX_FILTER)
hexa = ' '.join([f'{ord(c):02X}' for c in word])
hexwidth = length*3
results.append(f'{i:04x} {hexa:<{hexwidth}} {printable}')
if show:
for line in results:
print(line)
else:
return results
print(hexdump("python rocks\n and prxies roll\n"))
if isinstance(src, bytes):
src = src.decode()
如果我們有字串,解碼它(decode it)
word = str(src[i:i+length])
分別拾取字串中的一塊,並丟進變數 word 。
Grab a piece of the string to dump and put it into the word variable.
printable = word.translate(HEX_FILTER)
hexa = ' '.join([f'{ord(c):02X}' for c in word])
hexwidth = length*3
Reference參考資料
推薦影片
絕讚! Youtube 教學影片 | Elevate Cyber
原始碼
Github - Python For Cybersecurity | Monles
